Could we ever send data with complete security and secrecy online? Jon Cartwright taps into the latest developments towards a “quantum internet”.
Ten years. That’s how little time we have, or so it’s commonly believed, before quantum computers could potentially hack into all our supposedly private Internet data – whether it’s e-mails, medical records, bank transactions or government secrets. Information streaming down fibre-optic cables to every corner of the world, which is currently secure against the most powerful supercomputer decoders, will suddenly become visible to anyone with the right quantum tech.
At the end of last year, however, a team of researchers in China – led by Bao Yan from the State Key Laboratory of Mathematical Engineering and Advanced Computing in Zhengzhou – hit the headlines when they published details of a new algorithm that, they claim, makes classical encryption vulnerable even to the quantum computers of today (arxiv.org:2212.12372). Their research, which is yet to be peer-reviewed, has been challenged by some in the field. But the underlying message is clear: the quantum “bomb” could go off sooner than we think.

In fairness, quantum-technology experts have been raising the alarm for years about the dangers posed by quantum computers to information security. In 2020, for example, the UK’s National Cyber Security Centre published a white paper, which said that large companies and organizations “should factor the threat of quantum computer attacks into their long-term roadmaps” and start prioritizing systems for a transition to quantum-safe platforms.
Then in January 2023, the US computing giant IBM, which owns what is currently the world’s largest quantum computer, the 433-qubit Osprey, published its own report Security in the Quantum Computing Era. In the document, the company said that quantum computing is an “existential threat” to classical data security. “Make no mistake,” IBM warned. “The impact is coming – and it’s not a question of if, but how soon and how disruptive.”

Setting the scene for a quantum marketplace: where quantum business is up to and how it might unfold
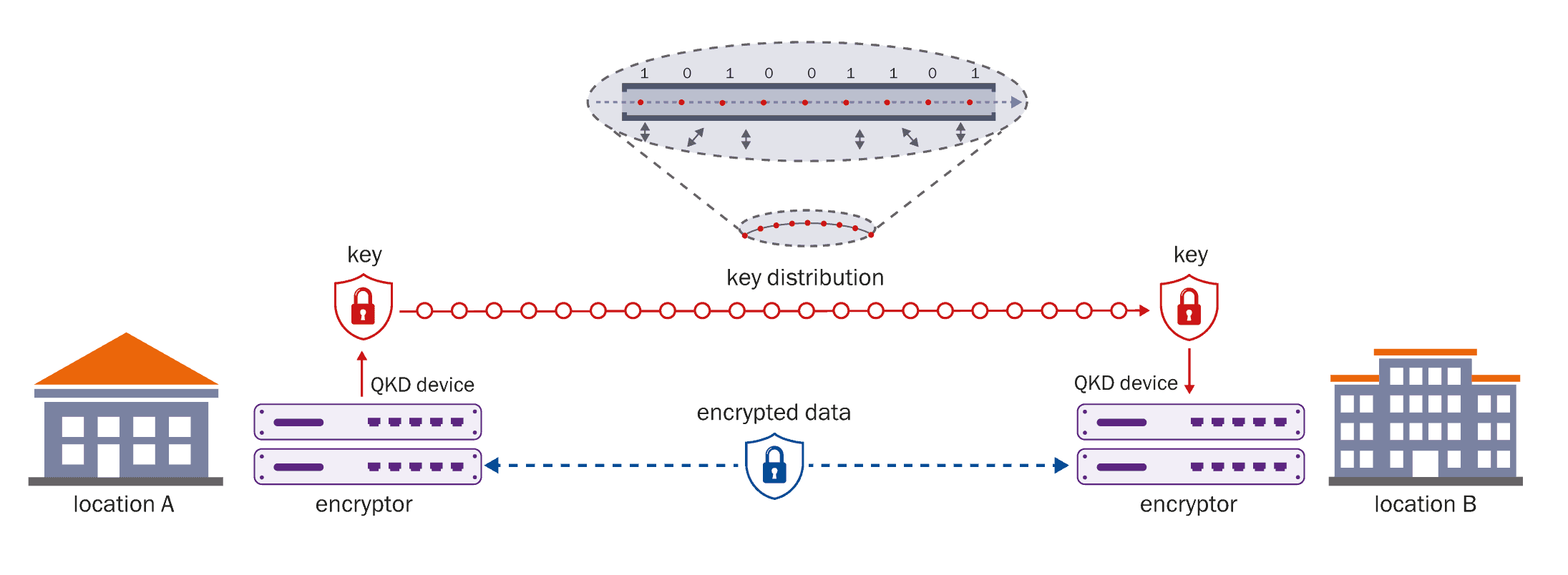
For proven security against quantum attacks, only quantum defences will do. Fortunately, physicists have long been developing quantum cryptography – and in particular quantum key distribution (QKD) – in readiness for a “post-quantum” world where quantum computers are everywhere. The beauty of QKD, which encrypts data using the quantum properties of photons, is that it guarantees the security of the keys used to scramble data while those keys are in transit.
In 2004 Id Quantique became the first company to secure a bank transfer via QKD and now there are dozens of businesses offering QKD products, with QKD-based networks quickly getting bigger and ever more complex. Japanese electronics giant Toshiba and UK telecoms firm BT have already developed a QKD network across a distance of 30km, from central London to Slough. Accounting giants Ernst and Young (EY) became the first customer last year when the firm used the network to send data between two of its offices – one at Canary Wharf and the other at London Bridge.
Spanning an area roughly 600 km2, the BT/Toshiba network is a big step forward for commercial QKD, but it’s just one part of a spreading global web of quantum traffic. National commercial QKD networks are likely to emerge within a few years, and at some future point we will see a “quantum internet”. This will be a global, quantum-secured information super-highway, connecting quantum as well as classical computers; through which anyone can share sensitive data without fear that it may one day be hacked.
But just how close are we to that tantalizing prospect? And is it truly realizable at all?
The key to secrecy
It’s not difficult to encrypt data. On today’s Internet, that’s usually done using the Advanced Encryption Standard (AES) algorithm, which was developed at the US National Institute of Standards and Technology in 2001. Once you’ve encrypted your information with a key linked to the algorithm, you simply send the data over the Internet to someone else, who decrypts it using the same key.

Turning a quantum advantage: IBM’s Jay Gambetta on seamlessly integrating quantum and classical computing
It’s almost impossible for anyone to decode the data without the secret key. That all sounds great – but how do you share the key without someone getting their hands on it first? In principle, you could take the key in, say, a briefcase or send it via homing pigeon. But for practical global communications the key is sent over the existing public fibre-optic network.
That’s obviously a bit risky, so the key itself is encrypted using “public key cryptography”. The most common way of securely exchanging the key is using the RSA algorithm, named after the computer scientists Ron Rivest, Adi Shamir and Leonard Adleman, who invented it in 1977. In fact, RSA is responsible for almost all secure Internet traffic these days as you can tell from the “https” at the start of a URL.
RSA encrypts the AES key by generating two further keys – one public, one private – making three in total. The public key is available to anyone, but only the person with the private key can unscramble the information. Someone wanting to obtain the AES key just needs to broadcast a public key, wait for the AES key to be sent back with this public encryption, and then decode it using his or her private key.
RSA keys are generated by multiplying large prime numbers, before being used to encrypt data according to a simple mathematical formula. Using conventional classical computing devices, it is very difficult to find the factors of the keys in order to decrypt the data, which is why data can be sent securely right now. In fact, it has been estimated that even the best supercomputers would take billions of years to crack the present RSA standard, which has key sizes of 2048 bits (numbers more than 600 digits long).
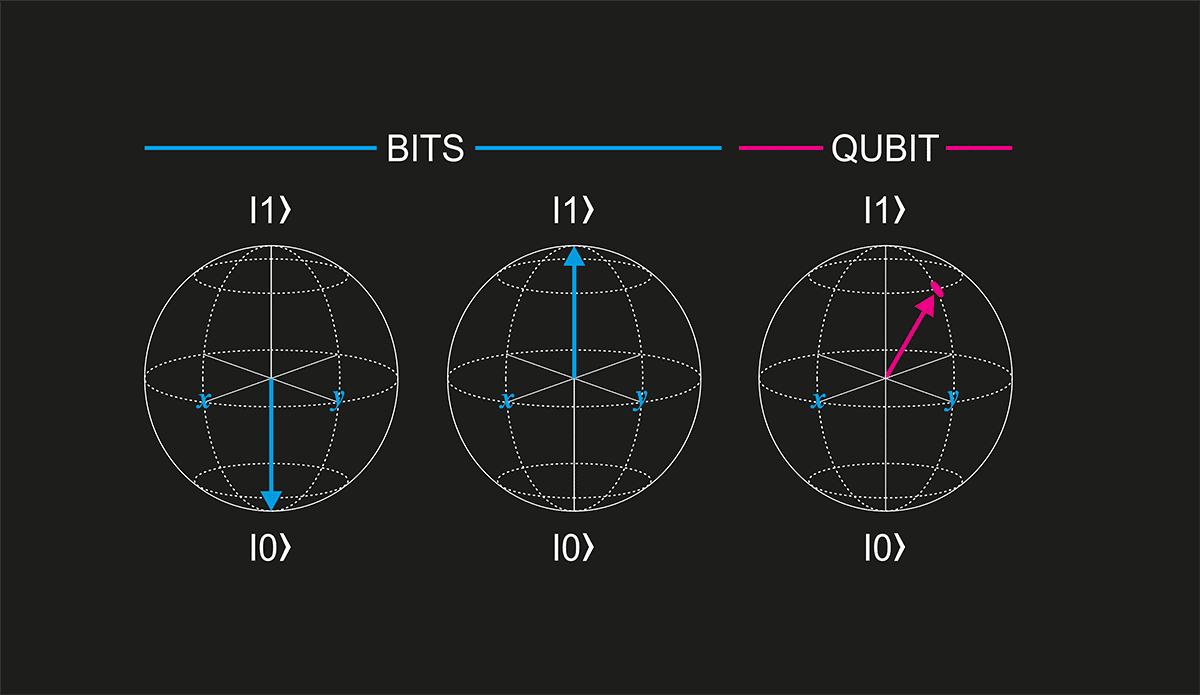
Quantum computers, by contrast, can factorize large numbers quickly and easily – undermining much of classical cryptography and potentially putting the security of the Internet at risk. Quite how many quantum bits, or “qubits”, a quantum computer would need to break RSA-2048 is, however, a matter of debate. Until recently, it was thought several thousand would be required. According to Yan’s new paper, however, you’d need only 372 qubits, placing the milestone squarely within reach of IBM’s Osprey, which has 433 qubits.

Democratizing the quantum ecosystem: Microsoft’s Krysta Svore on the pathway towards a scalable quantum computer
IBM has not yet commented on this danger, but the bigger worry is not whether anyone’s got a massive enough quantum computer right now. Hackers who want to wreak havoc just need to store encrypted data now – and then sit tight and wait until a powerful enough quantum device comes along to do the cracking. It’s what’s known as the “harvest now, decrypt later” approach.
One solution to this problem is to design new protocols that are more resistant to attacks from quantum computers. Based on various schemes that don’t need factorization, this form of “post-quantum cryptography” is being actively developed, with new standards expected to emerge in the next year or so. But the integrity of these protocols depends on various assumptions about the practical limits of quantum computers – assumptions that may be acceptable to most users, but not all.
The bottom line is that QKD is the only method of key distribution that is proven to be secure in principle. In essence, therefore, we want to move from “AES + RSA” to “AES + QKD” or AES and some other form of post-quantum cryptography.
Industrial impact

With its origins in quantum physics, it’s not surprising that physicists are at the forefront of work towards a quantum internet. Prominent among these is Andrew Shields, who joined Toshiba Europe’s Cambridge Research Laboratory in 1993. Today he heads the lab’s quantum technology division and in 2022 won the Katharine Burr Blodgett medal and prize from the Institute of Physics, an award that recognizes outstanding contributions to applied physics in industry.
Shields says that people outside quantum physics who manage large volumes of data are finally beginning to grasp the threat of quantum computing to data security. “Awareness is definitely increasing,” he says. “It’s on their radar now.” Back when Shields started out, most attention focused on the world’s first QKD protocol. Known as BB84, it had been proposed in 1984 by theoretical physicists Charles Bennett at IBM and Gilles Brassard at the University of Montreal.
In the BB84 protocol, the qubits exist in the form of the polarization states of individual photons – for example “0” being a horizontally polarized photon and “1” being vertically polarized. Once a sender has sent a secret key consisting of a string of these polarization states to a receiver, the recipient can work out if anyone has been eavesdropping on the message. That’s because quantum mechanics dictates that such an observation would indelibly change the state of what is being observed.
The BB84 protocol is foolproof, but in practice it is very difficult to generate or transmit strings of single photons over long distances. That’s why the quantum network recently developed by Shields and his colleagues at Toshiba, in collaboration with BT, uses a different protocol for QKD. It relies on weak laser pulses that contain not one but several photons in the same polarization state (see figure).
Quantum key distribution with a single photon stream
Trouble is, if a key is encoded via a pulse with two or more photons, there’s a risk that one of the photons could be intercepted without affecting the integrity of the others, rendering those bits insecure. The solution to this conundrum was proposed in 2003 by Hoi-Kwong Lo at the University of Toronto and Xiang-Bin Wang, who was then at the Quantum Computation and Information Project in Tokyo. Based on earlier work by Won-Young Hwang at Northwestern University in the US, it involves interspersing the true key photon-pulses with even weaker “decoy” laser pulses.
There have been a lot of advances in single and entangled photon sources, but it is still most efficient to use weak lasers
Andrew Shields, Toshiba
Now, if an eavesdropper tries to siphon off some of the total signal, they will remove fewer photons from the decoy than the signal pulse, altering their ratio in the overall mix – a tell-tale signature that the receiver can detect. In fact, this decoy-pulse protocol is the new standard for long-distance QKD. Toshiba currently uses it for all its QKD products, including those in the Toshiba–BT metro network.
“There have been a lot of advances in single and entangled photon sources, but it is still most efficient to use weak lasers,” says Shields. “Using the decoy protocol, we can get very close to the ideal key rate predicted for using a true single-photon source.”
Indeed, in Toshiba’s commercially available QKD systems, keys can be generated, sent, received and processed thousands of times per second. It has even developed a QKD “multiplexing” technology, in which qubit photons can be sent and received alongside classical communications photons at different wavelengths. Essentially, there is one band of wavelengths for the QKD keys and another band for the classical signal.
“Quantum channels will have to use the existing communications infrastructure, as replacing it will not be realistic from a cost perspective,” says Shields. “All of our work, both for a quantum-secure network or the quantum internet, is directed at using the existing infrastructure.” In fact, it is not absolutely necessary to share the same physical fibre-optic cable channels even with existing infrastructure. That’s because Internet and other data are mostly transmitted over bundles of fibre-optic cables, not all of which are currently employed or “lit”.
Still, there is a strong argument for sharing infrastructure to maximize its future potential and allow QKD to reach the edges of networks, where channels peter out into single fibres. In the UK, as in most countries, fibre has not yet completely taken over from older copper cabling – and is not expected to do so until 2025.
Making quantum networks
Building on an earlier point-to-point trial in Bristol, UK, the Toshiba–BT quantum metro network links three existing core nodes: one in London’s West End, one in the City of London, and one 30 km west in Slough. According to the physicist Andrew Lord, who is senior manager of optical research at BT, anyone within a 10–15 km radius of one of the three nodes can now sign up to transmit data via QKD. However, this capability has not come about easily.
Our bread and butter is transmitting classical data, encrypted or not, from customer to customer. The question is, how do you add quantum to that?
“Our bread and butter is transmitting classical data, encrypted or not, from customer to customer,” he says. “The question is, how do you add quantum to that? There are issues about the management of the quantum signal, making sure the right key hits the right end point. Then the standard WDM [wavelength division multiplexing] data channel has to be modified, too.”
The main problem is that shining high-powered lasers down a fibre can easily interfere with delicate quantum states. “Classical data swamps the quantum channel if we aren’t careful,” says Lord. “We’ve had to work with the WDM manufacturers to optimize that side of the network. It’s a very careful design that’s been needed to make it all happen.”

According to Lord, the network has been running since June 2022 without fail. Apart from involving accountants EY, the partnership has also attracted interest from elsewhere in the financial sector and from healthcare firms, as well as the government. It all helps Lord, Shields and their colleagues at BT and Toshiba determine what the market wants from a quantum network – and how to create a national, quantum-wide service.
BT is currently concluding a UK government-backed feasibility study that will put a price-tag on this kind of nationwide network using existing technology. But to develop an international network, which might well need transatlantic links, this technology will soon run out of steam. The quantum signals are weak to begin with, and the rate at which they refresh the keys slows 10-fold for every 50 km.

Securing the key to our quantum future
There are two ways forward, one of which is QKD via satellite. In 2020, researchers in China, led by Jian-Wei Pan from the University of Science and Technology of China, used the Micius satellite to establish QKD between Delingha in Qinghai province and Nanshan in Xinjiang province, which is over 1100 km away (Nature 582 501). But satellite QKD is not straightforward. Micius orbits the Earth at an altitude of just 500 km and passes over its groundstations for only five minutes every night, stopping the keys from being continually refreshed. Higher orbits can provide longer coverage, but the satellite and groundstation would be further apart and the signal would be even weaker. Nevertheless, BT has an agreement with the London-based quantum startup ArQit to explore the potential of satellite QKD, with possible launches in the next two years.
The second way forward is to use “quantum repeaters”. These devices sit in the middle of long-distance channels, and distribute pairs of photons that have entangled properties to opposite ends of the channel. An input photon can be made to interact with one of these entangled photons, teleporting its state onto the distant twin of the entangled photon pair at the other end of the channel. The repeater thereby acts as a bridge that can extend the maximum distance over which a quantum signal can be transmitted.
But while partial aspects of quantum repeaters have been demonstrated, a fully working one is yet to be realized. Having successfully implemented basic QKD on integrated-silicon photonic technology last year, Toshiba is now working on an integrated-silicon quantum repeater, Shields says.
Invisible success?
Currently, then, there is no trouble-free path to a quantum internet. But technology is fast progressing, and in recent years big money has started to flood in. In 2018 the European Union announced that it would spend at least €1bn over the next 10 years on its Quantum Flagship drive to boost quantum technology. This year alone, the US has set aside almost $850m for quantum R&D, with much more feeding in privately via the likes of computing giants such as Google, IBM and Microsoft. The UK is investing heavily, too, with the government promising £2.5bn for quantum technology in its second 10-year quantum strategy, which it hopes will generate an additional £1bn of private investment. Dwarfing all these public investments, however, is China, which is reportedly allocating more than ¥105bn (about £12.5bn) to quantum R&D in its latest five-year plan.
It could be that some version of a quantum internet is with us before the decade is out. But the irony for those working on it is that only failure, not success, will get noticed. If they succeed, our sensitive data will not be hacked, and most people will be none the wiser that quantum computers ever posed such a threat.




